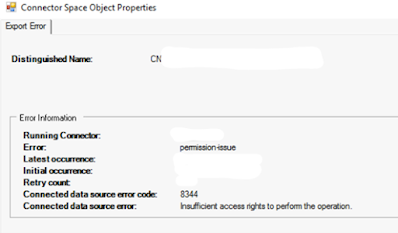
Office Suite 32/64 Determining version with CMD

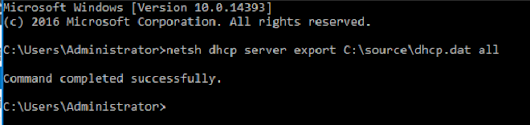
Open CMD Prompt as an administrator and browse to the following folder If this folder exists you are likely running 32 bit: cd c:\Program Files (x86)\Microsoft Office\Office16\ If this folder exists you are likely running 64 bit: cd c:\Program Files\Microsoft Office\Office16\ From either folder run the following command: cscript ospp.vbs /dstatus It will then show you the Office version information: Credit: https://learn.microsoft.com/en-us/microsoft-365/troubleshoot/licensing/determine-office-license-type?tabs=windows